Cybersecurity has emerged as a critical worry in the rapidly changing environment of automobile technology. The potential attack surfaces of cars increase with increased automation and connectivity, rendering them increasingly vulnerable to cyber assaults. To reduce these risks, the industry uses a range of cybersecurity strategies, one of which is Threat Analysis and Risk Assessment (TARA). This procedure is essential for spotting possible hazards, assessing their effects, and implementing preventative measures.
What is TARA in Automotive Cybersecurity?
TARA (Threat Analysis and Risk Assessment) is a systematic method for identifying, assessing, and prioritizing hazards in automotive systems. It is a crucial step in the cybersecurity lifecycle since it gives engineers and manufacturers insight into potential weak points in their systems and how to strengthen them.
- Asset Identification: Knowing what has to be safeguarded (communication systems, ECUs, etc.).
- Threat Identification: Identifying possible points of attack and threats.
- Risk Assessment: Evaluating the likelihood and impact of each threat.
- Risk Treatment Implementing measures to mitigate identified risks.
The Role of Attack Trees in TARA
Simulators facilitate rapid iteration by enabling quick adjustments based on simulation results, thus accelerating the development process and enhancing the fine-tuning of ADAS and AV systems.
Attack trees help in visualizing complex attack scenarios, making it easier for engineers to understand potential vulnerabilities and how they might be exploited. They can prioritize threats based on their likelihood and impact, guiding the focus of the TARA process.
Example of an Attack Tree:
- Root Node(Objective): Compromise Vehicle Braking System
- Branch 1(Method 1): Gain Physical Access to Vehicle
- Leaf 1.1(Step 1): Break into the car.
- Leaf 1.2(Step 2): Access the OBD-II port.
- Branch 2(Method 2): Exploit Wireless Communication
- Leaf 2.1(Step 1): Intercept wireless communication.
- Leaf 2.2(Step 2): Inject malicious commands via CAN bus.
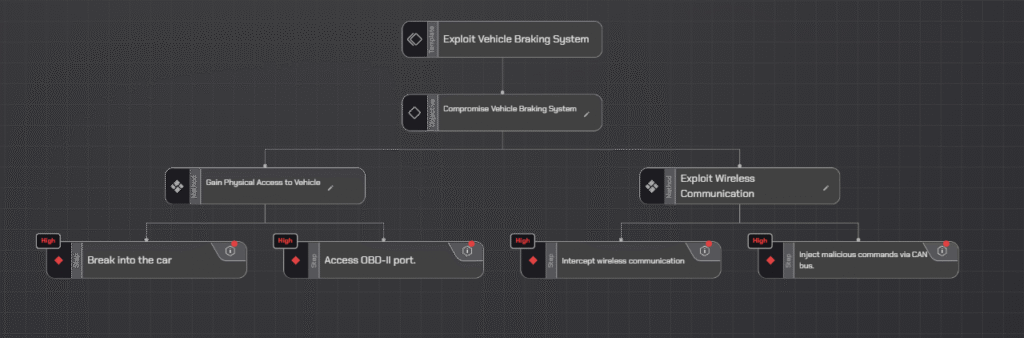
This structure allows the identification of potential security gaps in both physical and wireless aspects of the vehicle’s braking system.
Impact Rating in Automotive Cybersecurity
Impact ratings are a critical part of the TARA process, as it help determine the severity of a potential attack. It answers the question: If this attack were successful, how bad would the consequences be?
In automotive cybersecurity, impact ratings often consider factors such as:
- Safety: How many lives could be at risk?
- Financial Loss: What would the financial impact be on the manufacturer or users?
- Privacy: Would personal data be exposed?
- Operational Disruption: Could the attack disrupt the vehicle’s functionality?
Impact ratings typically range from low to high, and they influence the prioritization of risk mitigation efforts. High-impact threats may require immediate and significant countermeasures, while lower-impact threats might be addressed later or with less urgency.
Integrating Attack Trees and Impact Ratings in TARA
By integrating attack trees and impact ratings into the TARA process, cybersecurity teams can more effectively evaluate and prioritize threats. For example, if an attack tree reveals a high likelihood of a successful exploit, and the impact rating for that exploit is high (e.g., loss of life), it becomes a top priority for risk treatment.
Example TARA Process Using a House Analogy
Consider a house as a system where the goal is to protect it from burglars.
- Assets: Doors, windows, valuable items inside, security system.
- Threats: Break-ins, vandalism, data theft via smart home devices.
- Attack Tree:
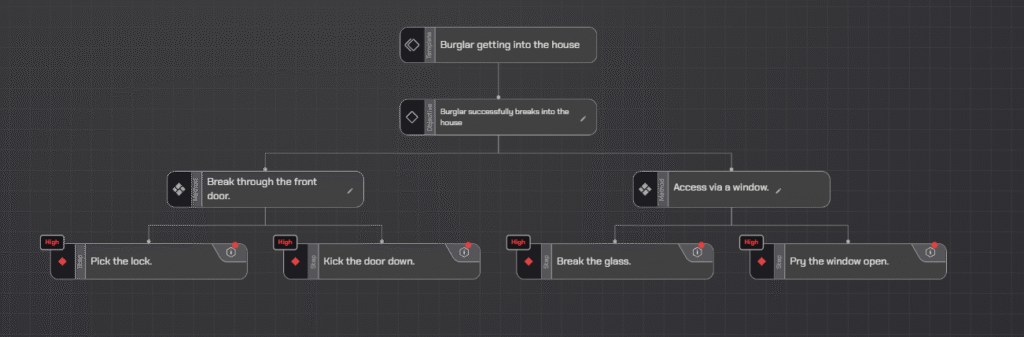
- Root Node(Objective): Burglar successfully breaks into the house.
- Branch 1(Method 1): Break through the front door.
- Leaf 1.1(Step 1): Pick the lock.
- Leaf 1.2(Step 2): Kick the door down.
- Branch 2(Method 1): Access via a window.
- Leaf 2.1(Step 1): Break the glass.
- Leaf 2.2(Step 2): Pry the window open.
Impact Rating:
- Safety: High (risk to life if occupants are home).
- Financial Loss: Medium to High (depending on valuables stolen).
- Privacy: Medium (access to personal data via smart devices).
- Operational Disruption: Low (unless the security system is compromised).
Risk Treatment:
- Mitigation for Door Attack: Install reinforced doors, and deadbolts.
- Mitigation for Window Attack: Use shatterproof glass, and install window sensors.
This analogy illustrates how TARA, attack trees, and impact ratings can be applied in a structured manner to protect a system—whether it’s a house or a vehicle—from potential threats.
Conclusion
By employing methodologies like attack trees and impact ratings, teams can effectively address vulnerabilities, prioritize risks based on their potential impact, and implement appropriate countermeasures, ensuring robust protection for vehicles and their users in a connected environment.
Author